Securing the Unconnected: Air Gap Windows Application Code Review and Developer Training Success
Client Background
Our partner, New Oceans Enterprises, is led by Donna Gallaher, an experienced cybersecurity leader with extensive executive experience. New Oceans Enterprises was engaged by a client in a regulated industry to act as their vCISO. The task was to develop a comprehensive security program to comply with their customer security requirements and regulatory demands. This client was mandated to undergo a thorough security audit for contract compliance. One stumbling block was that the architecture of their solution was not aligned with the assumptions made by the mandate. Additionally, the client was mandated to demonstrate that their developers had undergone appropriate security training.
Client’s Tech Stack
The client’s technology stack was a bit unorthodox in that it was a Windows desktop network application designed for an air-gapped network. It was built on top of the Microsoft .NET platform with a significant portion of the code built using Microsoft Visual Basic. There was no web application functionality. The primary security is provided by their customer’s network security practices and not an ongoing operation of servers by the client.
Challenges
The engagement presented several challenges:
- Misalignment of assumptions: The contractual mandate made specific assumptions that did not apply to the technology.
- Finding an appropriate review methodology: It was not clear how, or by what standard, the security of a Windows desktop application running in an air-gapped network could be reviewed.
- Tight timeline and small team: The timeline for this engagement was critical. A major contract was in the balance and the client wanted to meet the contractual obligations and continue the business relationship with their client. Additionally, the small team meant that taking up too much time and resources to undergo traditional threat modeling exercises from scratch was not appropriate.
The Rietta Solution
Despite these challenges, Rietta successfully engaged to provide a thorough risk-based assessment and code review of the application. For the assessment, we adapted the OWASP Mobile Application Security Verification Standard (MASVS). We carefully documented each of the requirements and wrote clear explanations for those that were not applicable. For the thorough review, we:
- Interviewed all developers working on the application
- Conducted a thorough tool assisted and manual code review of the VB.NET source
- Reviewed the entire supply chain including the Microsoft-sourced dependencies and other DLLs from smaller vendors
- Identified critical areas for security improvements and communicated with the developers and management
- Documented the application, drawing data flow diagrams, and building out other threat modeling details to support clear communication about the security posture of the overall system
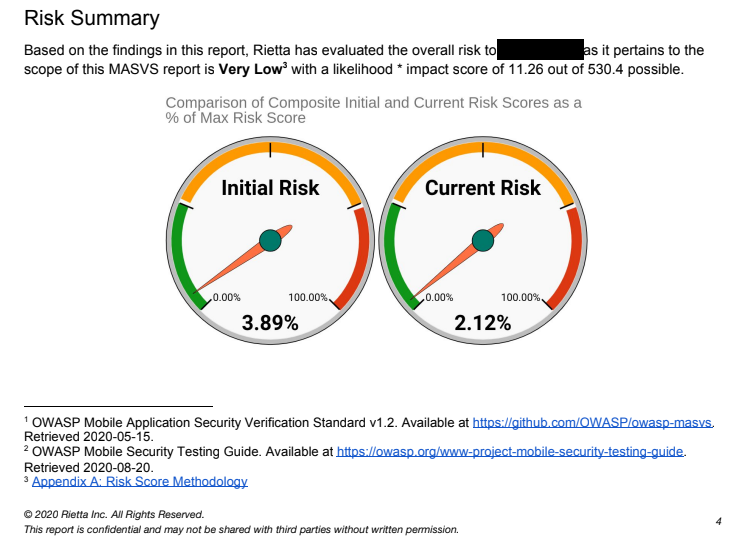
- By working closely with developers, they were actually able to make security improvements during the assessment, and the positive change in the risk score was reflected in the final report to management!
- Wrote a detailed MASVS findings report for the client’s executive management and development teams
- Wrote a short report suitable for sharing the client’s customers to satisfy their need to understand the audit results without oversharing sensitive details
- Wrote a signed bridge letter, on letterhead, attesting to the security posture of the application
After this reporting engagement, we also provided a 1.5 hour lunch and learn security seminar for the clients developers. This satisfied the mandatory cyber security training requirements included in the contractual obligations and regulations.
This engagement required significant technical experience both with security and software development.
Client Outcomes
Our solution was not only technically sound but also efficient and cost-effective. We used an open standard methodology to evaluate the security of the application, contextualized the requirements to the client’s specific needs, and successfully satisfied customer needs. This ultimately allowed a very significant financial deal to be completed on time.
Moreover, because of our thorough testing and validation processes, our partner New Oceans was confident in the success of the assessments. They were able to provide a full service solution to their client, implementing a successful full information security policy program.
